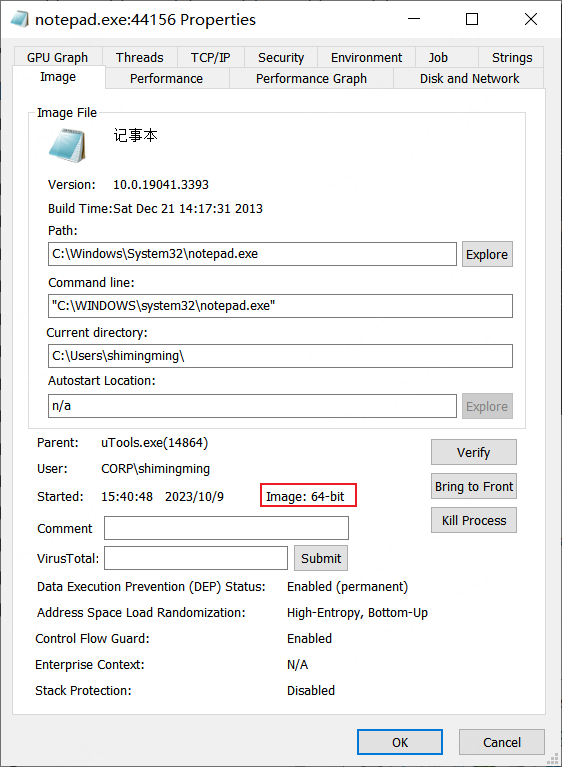
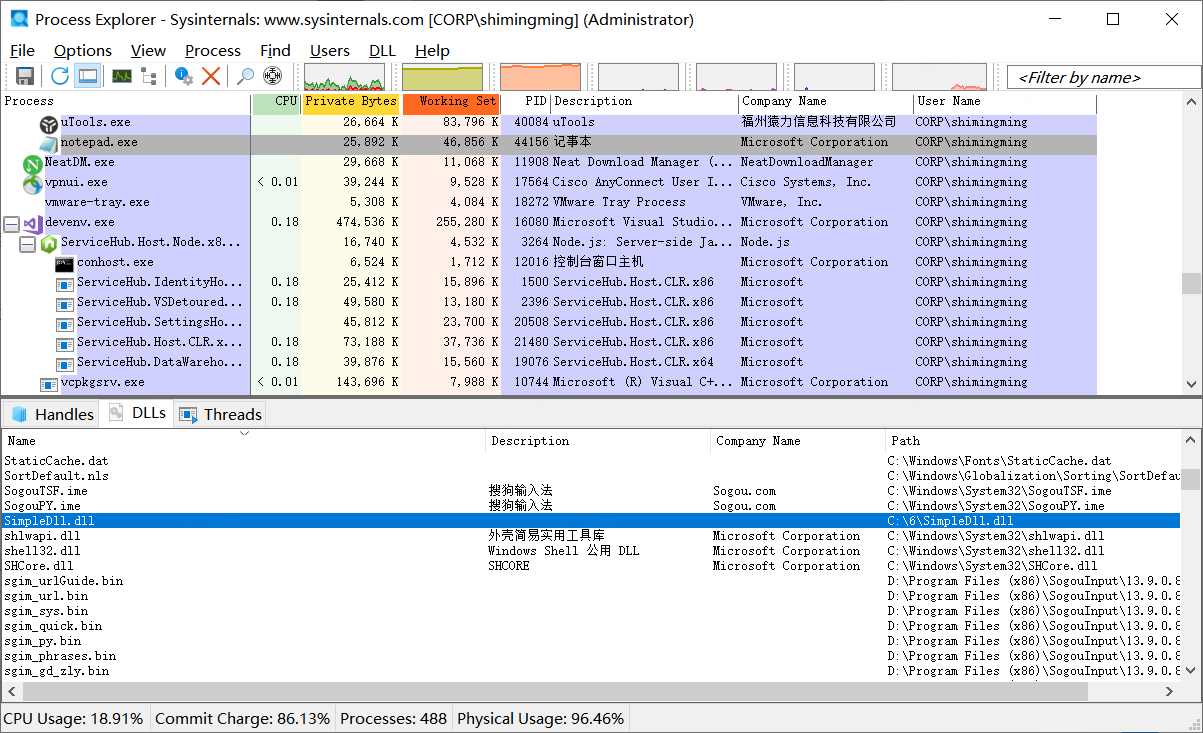
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
| #include <windows.h>
#include <iostream>
#include <tlhelp32.h>
using namespace std;
DWORD GetPidByName(LPCWSTR lpName)
{
DWORD pid = 0;
HANDLE hSnap = ::CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS, 0);
if (!hSnap)
{
cout << "Create Process Snap failed" << endl;
return 0;
}
PROCESSENTRY32 pe;
pe.dwSize = sizeof(PROCESSENTRY32);
Process32First(hSnap, &pe);
do {
if (!_wcsicmp(lpName, pe.szExeFile))
{
return pe.th32ProcessID;
}
} while (Process32Next(hSnap, &pe));
return pid;
}
bool EnableDebugPrivilege()
{
bool bRet = false;
HANDLE token;
TOKEN_PRIVILEGES tp;
if (!OpenProcessToken(GetCurrentProcess(), TOKEN_ADJUST_PRIVILEGES | TOKEN_QUERY, &token))
{
cout << "Open Toekn Failed" << endl;
return bRet;
}
LUID luid;
if (!LookupPrivilegeValue(NULL, SE_DEBUG_NAME, &luid))
{
cout << "Get uid failed" << endl;
return bRet;
}
tp.PrivilegeCount = 1;
tp.Privileges[0].Attributes = SE_PRIVILEGE_ENABLED;
tp.Privileges[0].Luid = luid;
if (!AdjustTokenPrivileges(token, 0, &tp, sizeof(TOKEN_PRIVILEGES), NULL, NULL))
{
cout << "Adjust Privilege failed" << endl;
return bRet;
}
bRet = true;
return bRet;
}
int main(char* argc, const char* argv[])
{
if (!EnableDebugPrivilege())
{
cout << "提权失败" << endl;
return 0;
}
DWORD dwTargetPid = GetPidByName(L"notepad.exe");
if (!dwTargetPid)
{
cout << "Get Target Process Id failed" << endl;
return 0;
}
HANDLE hTarget = OpenProcess(PROCESS_ALL_ACCESS, false, dwTargetPid);
if (!hTarget)
{
cout << "Open Target Process failed" << endl;
return 0;
}
void* pLoadLibFuncParam = nullptr;
pLoadLibFuncParam = VirtualAllocEx(hTarget, 0, 4096, MEM_COMMIT | MEM_RESERVE, PAGE_READWRITE);
if (pLoadLibFuncParam == nullptr)
{
cout << "alloc memery failed" << endl;
CloseHandle(hTarget);
return 0;
}
LPCTSTR lpParam = L"C:\\6\\SimpleDll.dll";
if (!WriteProcessMemory(hTarget, pLoadLibFuncParam, (LPCVOID)lpParam, (wcslen(lpParam) + 1) * sizeof(TCHAR), NULL))
{
cout << "写入内存失败" << endl;
CloseHandle(hTarget);
return 0;
}
HMODULE hNtdll = LoadLibrary(L"kernel32.dll");
if (!hNtdll)
{
cout << "加载模块错误" << GetLastError() << endl;
CloseHandle(hTarget);
return 0;
}
cout << "模块句柄: " << hNtdll << endl;
void* pLoadLibrary = nullptr;
pLoadLibrary = GetProcAddress(hNtdll, "LoadLibraryW");
if (pLoadLibrary == nullptr)
{
cout << "找不到函数" << endl;
CloseHandle(hTarget);
return 0;
}
cout << "函数地址: " << pLoadLibrary << endl;
DWORD dwThreadId = 0;
HANDLE hRemoteThread = CreateRemoteThread(hTarget, NULL, 0, (LPTHREAD_START_ROUTINE)pLoadLibrary, (LPVOID)pLoadLibFuncParam, 0, &dwThreadId);
if (!hRemoteThread)
{
cout << "创建进程失败" << GetLastError() << endl;
CloseHandle(hTarget);
return 0;
}
cout << "运行结束" << hRemoteThread << endl;
getchar();
getchar();
CloseHandle(hTarget);
return 0;
}
|