概述:PEB是什么?以及PEB在进程中的实例
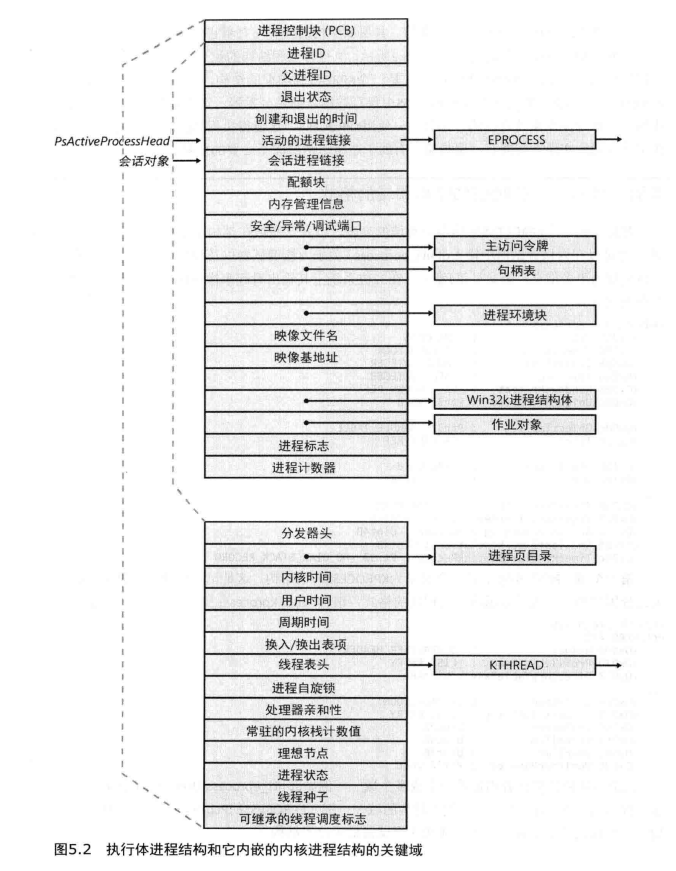
先看一下 执行体进程结构和它内嵌的内核进程结构的关键域 方便理解,具体的结构可使用 dt nt!_EPROCESS 查看
0x01、如何在windbg中查看该进程结构?
环境:windbg双机调试模式,相关步骤查找
windows双机调试或bcdsedit。以 notepad.exe(记事本) 为例,win+R 运行 notepad。输入以下命令得到 notepad 的进程相关信息
输出如下所示:
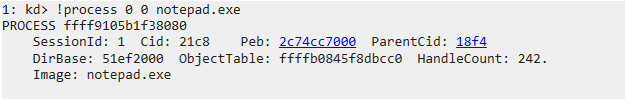
在这里获取到 notepad 的进程id为 ffff9105b1f38080。 有图可知,整个 notepad.exe 的保存结构为一个
_EPROCESS,进行下一步,查看进程:
输出如下所示:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
>No export openpid found
>1: kd> dt nt!_EPROCESS ffff9105b1f38080
>+0x000 Pcb : _KPROCESS
>+0x438 ProcessLock : _EX_PUSH_LOCK
>+0x440 UniqueProcessId : 0x00000000`000021c8 Void
>+0x448 ActiveProcessLinks : _LIST_ENTRY [ 0xffff9105`af299748 - 0xffff9105`af8484c8 ]
>+0x458 RundownProtect : _EX_RUNDOWN_REF
>+0x460 Flags2 : 0xd000
>+0x460 JobNotReallyActive : 0y0
>+0x460 AccountingFolded : 0y0
>+0x460 NewProcessReported : 0y0
>+0x460 ExitProcessReported : 0y0
>+0x460 ReportCommitChanges : 0y0
>+0x460 LastReportMemory : 0y0
>+0x460 ForceWakeCharge : 0y0
>+0x460 CrossSessionCreate : 0y0
>+0x460 NeedsHandleRundown : 0y0
>+0x460 RefTraceEnabled : 0y0
>+0x460 PicoCreated : 0y0
>+0x460 EmptyJobEvaluated : 0y0
>+0x460 DefaultPagePriority : 0y101
>+0x460 PrimaryTokenFrozen : 0y1
>+0x460 ProcessVerifierTarget : 0y0
>+0x460 RestrictSetThreadContext : 0y0
>+0x460 AffinityPermanent : 0y0
>+0x460 AffinityUpdateEnable : 0y0
>+0x460 PropagateNode : 0y0
>+0x460 ExplicitAffinity : 0y0
>+0x460 ProcessExecutionState : 0y00
>+0x460 EnableReadVmLogging : 0y0
>+0x460 EnableWriteVmLogging : 0y0
>+0x460 FatalAccessTerminationRequested : 0y0
>+0x460 DisableSystemAllowedCpuSet : 0y0
>+0x460 ProcessStateChangeRequest : 0y00
>+0x460 ProcessStateChangeInProgress : 0y0
>+0x460 InPrivate : 0y0
>+0x464 Flags : 0x144d0c01
>+0x464 CreateReported : 0y1
>+0x464 NoDebugInherit : 0y0
>+0x464 ProcessExiting : 0y0
>+0x464 ProcessDelete : 0y0
>+0x464 ManageExecutableMemoryWrites : 0y0
>+0x464 VmDeleted : 0y0
>+0x464 OutswapEnabled : 0y0
>+0x464 Outswapped : 0y0
>+0x464 FailFastOnCommitFail : 0y0
>+0x464 Wow64VaSpace4Gb : 0y0
>+0x464 AddressSpaceInitialized : 0y11
>+0x464 SetTimerResolution : 0y0
>+0x464 BreakOnTermination : 0y0
>+0x464 DeprioritizeViews : 0y0
>+0x464 WriteWatch : 0y0
>+0x464 ProcessInSession : 0y1
>+0x464 OverrideAddressSpace : 0y0
>+0x464 HasAddressSpace : 0y1
>+0x464 LaunchPrefetched : 0y1
>+0x464 Background : 0y0
>+0x464 VmTopDown : 0y0
>+0x464 ImageNotifyDone : 0y1
>+0x464 PdeUpdateNeeded : 0y0
>+0x464 VdmAllowed : 0y0
>+0x464 ProcessRundown : 0y0
>+0x464 ProcessInserted : 0y1
>+0x464 DefaultIoPriority : 0y010
>+0x464 ProcessSelfDelete : 0y0
>+0x464 SetTimerResolutionLink : 0y0
>+0x468 CreateTime : _LARGE_INTEGER 0x01d9f901`1100d7bf
>+0x470 ProcessQuotaUsage : [2] 0x3a58
>+0x480 ProcessQuotaPeak : [2] 0x3a98
>+0x490 PeakVirtualSize : 0x00000201`09c0f000
>+0x498 VirtualSize : 0x00000201`09c0f000
>+0x4a0 SessionProcessLinks : _LIST_ENTRY [ 0xffff9105`b1681520 - 0xffff9105`af848520 ]
>+0x4b0 ExceptionPortData : 0xffff9105`aa569da0 Void
>+0x4b0 ExceptionPortValue : 0xffff9105`aa569da0
>+0x4b0 ExceptionPortState : 0y000
>+0x4b8 Token : _EX_FAST_REF
>+0x4c0 MmReserved : 0
>+0x4c8 AddressCreationLock : _EX_PUSH_LOCK
>+0x4d0 PageTableCommitmentLock : _EX_PUSH_LOCK
>+0x4d8 RotateInProgress : (null)
>+0x4e0 ForkInProgress : (null)
>+0x4e8 CommitChargeJob : (null)
>+0x4f0 CloneRoot : _RTL_AVL_TREE
>+0x4f8 NumberOfPrivatePages : 0x238
>+0x500 NumberOfLockedPages : 0
>+0x508 Win32Process : 0xfffffe41`85f6d620 Void
>+0x510 Job : (null)
>+0x518 SectionObject : 0xffffb084`5ea9d3b0 Void
>+0x520 SectionBaseAddress : 0x00007ff6`477c0000 Void
>+0x528 Cookie : 0x4118bb70
>+0x530 WorkingSetWatch : (null)
>+0x538 Win32WindowStation : 0x00000000`000000b4 Void
>+0x540 InheritedFromUniqueProcessId : 0x00000000`000018f4 Void
>+0x548 OwnerProcessId : 0x18f6
>+0x550 Peb : 0x0000002c`74cc7000 _PEB
>+0x558 Session : 0xffffc180`6a1ec000 _MM_SESSION_SPACE
>+0x560 Spare1 : (null)
>+0x568 QuotaBlock : 0xffff9105`aa072cc0 _EPROCESS_QUOTA_BLOCK
>+0x570 ObjectTable : 0xffffb084`5f8dbcc0 _HANDLE_TABLE
>+0x578 DebugPort : (null)
>+0x580 WoW64Process : (null)
>+0x588 DeviceMap : 0xffffb084`5e99c190 Void
>+0x590 EtwDataSource : 0xffff9105`b4004550 Void
>+0x598 PageDirectoryPte : 0
>+0x5a0 ImageFilePointer : 0xffff9105`acb3fc30 _FILE_OBJECT
>+0x5a8 ImageFileName : [15] "notepad.exe"
>+0x5b7 PriorityClass : 0x2 ''
>+0x5b8 SecurityPort : (null)
>+0x5c0 SeAuditProcessCreationInfo : _SE_AUDIT_PROCESS_CREATION_INFO
>+0x5c8 JobLinks : _LIST_ENTRY [ 0x00000000`00000000 - 0x00000000`00000000 ]
>+0x5d8 HighestUserAddress : 0x00007fff`ffff0000 Void
>+0x5e0 ThreadListHead : _LIST_ENTRY [ 0xffff9105`af887a68 - 0xffff9105`aad93528 ]
>+0x5f0 ActiveThreads : 6
>+0x5f4 ImagePathHash : 0xc5670914
>+0x5f8 DefaultHardErrorProcessing : 1
>+0x5fc LastThreadExitStatus : 0n1
>+0x600 PrefetchTrace : _EX_FAST_REF
>+0x608 LockedPagesList : (null)
>+0x610 ReadOperationCount : _LARGE_INTEGER 0x0
>+0x618 WriteOperationCount : _LARGE_INTEGER 0x0
>+0x620 OtherOperationCount : _LARGE_INTEGER 0x30
>+0x628 ReadTransferCount : _LARGE_INTEGER 0x0
>+0x630 WriteTransferCount : _LARGE_INTEGER 0x0
>+0x638 OtherTransferCount : _LARGE_INTEGER 0x210
>+0x640 CommitChargeLimit : 0
>+0x648 CommitCharge : 0x31a
>+0x650 CommitChargePeak : 0x31a
>+0x680 Vm : _MMSUPPORT_FULL
>+0x7c0 MmProcessLinks : _LIST_ENTRY [ 0xffff9105`af299ac0 - 0xffff9105`af848840 ]
>+0x7d0 ModifiedPageCount : 1
>+0x7d4 ExitStatus : 0n259
>+0x7d8 VadRoot : _RTL_AVL_TREE
>+0x7e0 VadHint : 0xffff9105`ad4c8c20 Void
>+0x7e8 VadCount : 0x6a
>+0x7f0 VadPhysicalPages : 0
>+0x7f8 VadPhysicalPagesLimit : 0
>+0x800 AlpcContext : _ALPC_PROCESS_CONTEXT
>+0x820 TimerResolutionLink : _LIST_ENTRY [ 0x00000000`00000000 - 0x00000000`00000000 ]
>+0x830 TimerResolutionStackRecord : (null)
>+0x838 RequestedTimerResolution : 0
>+0x83c SmallestTimerResolution : 0
>+0x840 ExitTime : _LARGE_INTEGER 0x0
>+0x848 InvertedFunctionTable : (null)
>+0x850 InvertedFunctionTableLock : _EX_PUSH_LOCK
>+0x858 ActiveThreadsHighWatermark : 6
>+0x85c LargePrivateVadCount : 0
>+0x860 ThreadListLock : _EX_PUSH_LOCK
>+0x868 WnfContext : 0xffffb084`5fe9e180 Void
>+0x870 ServerSilo : (null)
>+0x878 SignatureLevel : 0 ''
>+0x879 SectionSignatureLevel : 0 ''
>+0x87a Protection : _PS_PROTECTION
>+0x87b HangCount : 0y000
>+0x87b GhostCount : 0y000
>+0x87b PrefilterException : 0y0
>+0x87c Flags3 : 0x41c000
>+0x87c Minimal : 0y0
>+0x87c ReplacingPageRoot : 0y0
>+0x87c Crashed : 0y0
>+0x87c JobVadsAreTracked : 0y0
>+0x87c VadTrackingDisabled : 0y0
>+0x87c AuxiliaryProcess : 0y0
>+0x87c SubsystemProcess : 0y0
>+0x87c IndirectCpuSets : 0y0
>+0x87c RelinquishedCommit : 0y0
>+0x87c HighGraphicsPriority : 0y0
>+0x87c CommitFailLogged : 0y0
>+0x87c ReserveFailLogged : 0y0
>+0x87c SystemProcess : 0y0
>+0x87c HideImageBaseAddresses : 0y0
>+0x87c AddressPolicyFrozen : 0y1
>+0x87c ProcessFirstResume : 0y1
>+0x87c ForegroundExternal : 0y1
>+0x87c ForegroundSystem : 0y0
>+0x87c HighMemoryPriority : 0y0
>+0x87c EnableProcessSuspendResumeLogging : 0y0
>+0x87c EnableThreadSuspendResumeLogging : 0y0
>+0x87c SecurityDomainChanged : 0y0
>+0x87c SecurityFreezeComplete : 0y1
>+0x87c VmProcessorHost : 0y0
>+0x87c VmProcessorHostTransition : 0y0
>+0x87c AltSyscall : 0y0
>+0x87c TimerResolutionIgnore : 0y0
>+0x87c DisallowUserTerminate : 0y0
>+0x880 DeviceAsid : 0n0
>+0x888 SvmData : (null)
>+0x890 SvmProcessLock : _EX_PUSH_LOCK
>+0x898 SvmLock : 0
>+0x8a0 SvmProcessDeviceListHead : _LIST_ENTRY [ 0xffff9105`b1f38920 - 0xffff9105`b1f38920 ]
>+0x8b0 LastFreezeInterruptTime : 0
>+0x8b8 DiskCounters : 0xffff9105`b1f38ac0 _PROCESS_DISK_COUNTERS
>+0x8c0 PicoContext : (null)
>+0x8c8 EnclaveTable : (null)
>+0x8d0 EnclaveNumber : 0
>+0x8d8 EnclaveLock : _EX_PUSH_LOCK
>+0x8e0 HighPriorityFaultsAllowed : 0
>+0x8e8 EnergyContext : 0xffff9105`b1f38ae8 _PO_PROCESS_ENERGY_CONTEXT
>+0x8f0 VmContext : (null)
>+0x8f8 SequenceNumber : 0xe9
>+0x900 CreateInterruptTime : 0xe8096541
>+0x908 CreateUnbiasedInterruptTime : 0xe8096541
>+0x910 TotalUnbiasedFrozenTime : 0
>+0x918 LastAppStateUpdateTime : 0xe8096541
>+0x920 LastAppStateUptime : 0y0000000000000000000000000000000000000000000000000000000000000 (0)
>+0x920 LastAppState : 0y000
>+0x928 SharedCommitCharge : 0xa2d
>+0x930 SharedCommitLock : _EX_PUSH_LOCK
>+0x938 SharedCommitLinks : _LIST_ENTRY [ 0xffffb084`5cc16358 - 0xffffb084`5e777688 ]
>+0x948 AllowedCpuSets : 0
>+0x950 DefaultCpuSets : 0
>+0x948 AllowedCpuSetsIndirect : (null)
>+0x950 DefaultCpuSetsIndirect : (null)
>+0x958 DiskIoAttribution : (null)
>+0x960 DxgProcess : 0xffffb084`5fe76de0 Void
>+0x968 Win32KFilterSet : 0
>+0x970 ProcessTimerDelay : _PS_INTERLOCKED_TIMER_DELAY_VALUES
>+0x978 KTimerSets : 0
>+0x97c KTimer2Sets : 0
>+0x980 ThreadTimerSets : 5
>+0x988 VirtualTimerListLock : 0
>+0x990 VirtualTimerListHead : _LIST_ENTRY [ 0xffff9105`b1f38a10 - 0xffff9105`b1f38a10 ]
>+0x9a0 WakeChannel : _WNF_STATE_NAME
>+0x9a0 WakeInfo : _PS_PROCESS_WAKE_INFORMATION
>+0x9d0 MitigationFlags : 0x21
>+0x9d0 MitigationFlagsValues : <anonymous-tag>
>+0x9d4 MitigationFlags2 : 0x40000000
>+0x9d4 MitigationFlags2Values : <anonymous-tag>
>+0x9d8 PartitionObject : 0xffff9105`a589c260 Void
>+0x9e0 SecurityDomain : 0x00000001`00000032
>+0x9e8 ParentSecurityDomain : 0x00000001`00000032
>+0x9f0 CoverageSamplerContext : (null)
>+0x9f8 MmHotPatchContext : (null)
>+0xa00 DynamicEHContinuationTargetsTree : _RTL_AVL_TREE
>+0xa08 DynamicEHContinuationTargetsLock : _EX_PUSH_LOCK
>+0xa10 DynamicEnforcedCetCompatibleRanges : _PS_DYNAMIC_ENFORCED_ADDRESS_RANGES
>+0xa20 DisabledComponentFlags : 0
>+0xa28 PathRedirectionHashes : (null)这里可以看到很多信息,比如进程的 Pcb(进程控制块)的结构体为
_KPROCESS。进程的映像名(ImageFileName)为notepad.exe
0x02、PEB与上述 _EPROCESS 的关系
上述看到的信息
_EPROCESS均位于系统空间中。而进程环境块(PEB)是一个比较特殊的存在,它位于进程的地址空间中。因为PEB的特殊性,比如环境变量、进程信息、线程等不同,因此PEB可以看做是一个私有的变量,定义了每个程序内部所需要的成员。有关PEB结构体可以在主页中搜索
WOW64通过PEB获取32/64位进程模块信息查看。
补充:
在 windbg 调试中,默认使用 !PEB 命令时,查看的是 CPU 0 上当前运行的线程所属进程的进程环境块(PEB)。 如果要查看具体某一进程的环境块,需要先切换到该进程空间,再使用 !PEB 命令查看。
PEB概述
PEB(Process Environment Block), 即进程环境块。不同于 EPROCESS和相关的数据结构(存储于系统空间中),进程环境块位于进程地址空间中(因为它包含一些需要由模式模式代码来修改的信息)。PEB包含了映像加载器、堆管理器以及其他需要从用户迷失访问它的Windows组件所需的信息。PEB域如下所示:
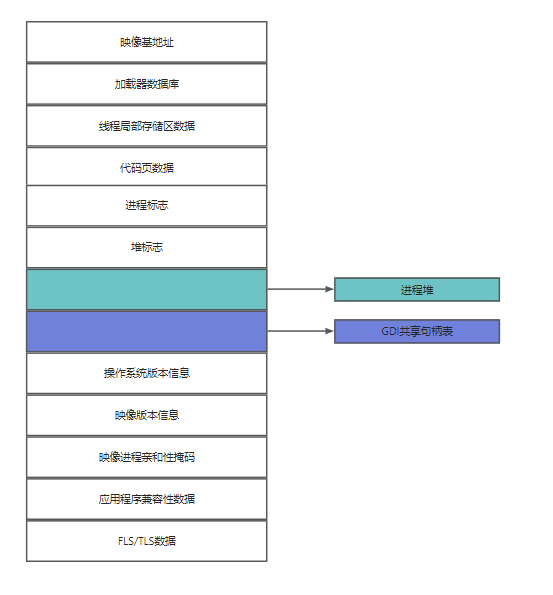
PEB 实例
在内核调试器中利用 !PEB 命令,你可以将 PEB 结构转储出来,会显示 CPU 0 上当前运行着的线程所属进程的PEB。
如下所示为进程 CPU 0 上运行线程所属进程的PEB
1 | 1: kd> !peb |
查看W32PROCESS
1 | 1: kd> dt win32k!_W32PROCESS ffffb98ae4682300 |
参考文献
- 《深入解析windows操作系统 第6版》
